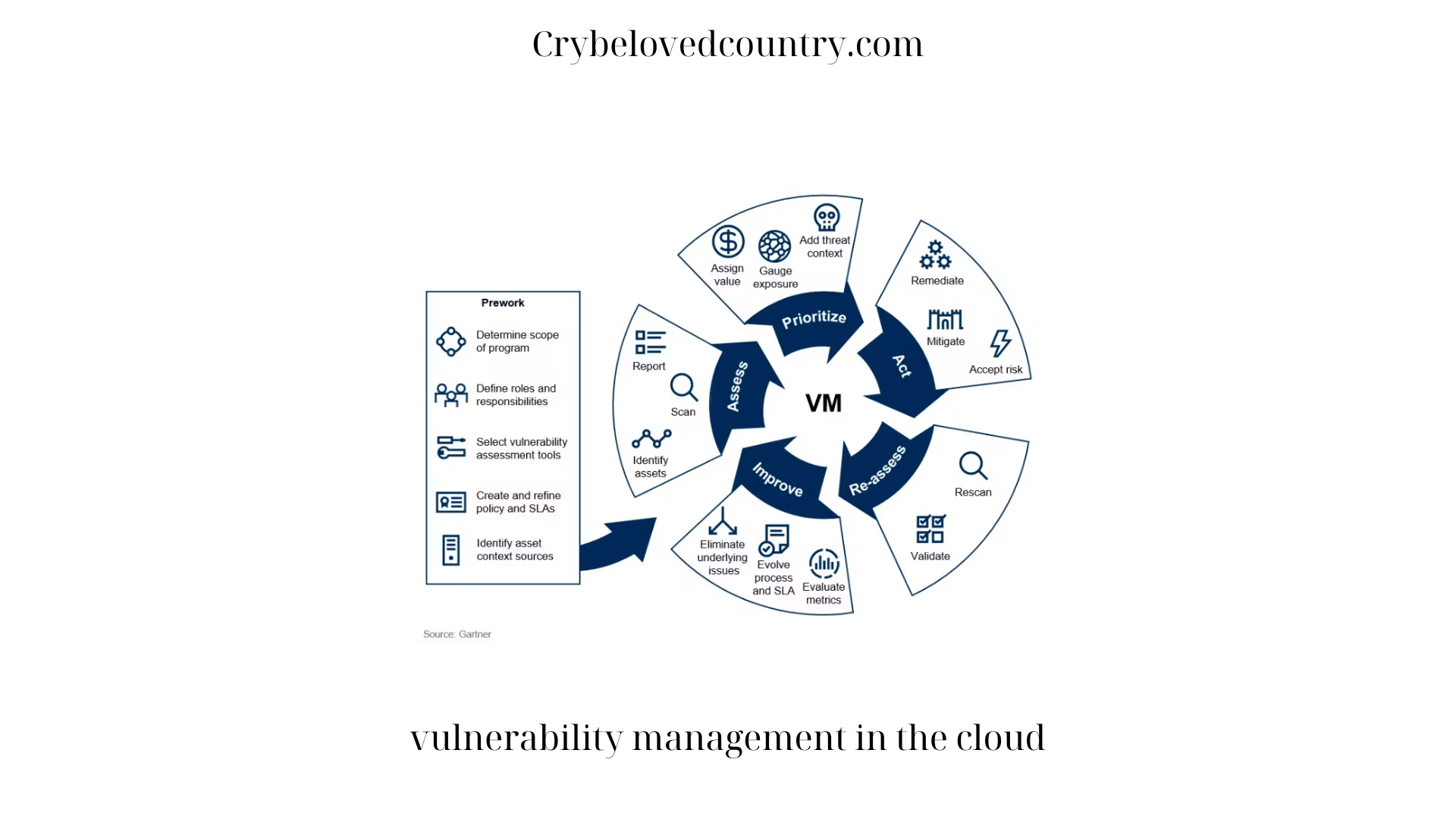
With the increasing adoption of cloud computing, organizations are reaping the benefits of scalability, flexibility, and cost efficiency. However, as more data and critical applications migrate to the cloud, the need for robust security measures becomes paramount. One crucial aspect of cloud security is vulnerability management. In this article, Crybelovedcountry will delve into the best practices for vulnerability management in the cloud, enabling organizations to proactively identify and address potential weaknesses in their cloud environments.
Vulnerability Management in the Cloud: Best Practices for Securing Your Environment

- Understand the Shared Responsibility Model
When it comes to cloud security, it’s essential to grasp the shared responsibility model. Cloud service providers (CSPs) are responsible for security “of” the cloud, which includes the physical infrastructure, network, and hypervisor layers. On the other hand, customers are responsible for security “in” the cloud, which involves securing their applications, data, and operating systems. By understanding this model, organizations can delineate their responsibilities and ensure comprehensive vulnerability management in the cloud.
- Conduct Regular Vulnerability Assessments
Regular vulnerability assessments are a cornerstone of effective vulnerability management. These assessments involve scanning the cloud environment for known vulnerabilities, misconfigurations, and weaknesses that could potentially be exploited by attackers. By leveraging automated vulnerability scanning tools, organizations can identify and prioritize vulnerability management in the cloud based on their severity and potential impact. Conducting these assessments on a scheduled basis helps ensure continuous visibility into the security posture of the cloud environment.
- Implement Patch Management Processes
After identifying vulnerabilities through assessments, it is crucial to promptly address them by implementing robust patch management processes. Cloud environments are dynamic, with frequent updates and new vulnerability management in the cloud emerging regularly. Organizations should establish a systematic approach to patching, which includes evaluating the criticality of patches, testing them in non-production environments, and deploying them efficiently across the cloud infrastructure. By staying up to date with patches, organizations mitigate the risk of known vulnerabilities being exploited.
- Employ Secure Configuration Management
Misconfigurations are a common cause of cloud security breaches. It is imperative to establish secure configuration management practices to minimize the risk of misconfigured cloud resources. This involves adhering to industry best practices and security frameworks, such as the Center for Internet Security (CIS) benchmarks, to configure cloud services securely. Automated configuration management tools can help enforce consistency across cloud resources, reducing vulnerability management in the cloud the likelihood of misconfigurations that may introduce vulnerabilities.
Effective vulnerability management requires proactive monitoring and analysis of cloud logs. Cloud vulnerability management in the cloud generate vast amounts of log data that can provide critical insights into potential security incidents and vulnerabilities. By leveraging security information and event management (SIEM) solutions and log analysis tools, organizations can detect anomalous activities, unauthorized access attempts, and indicators of compromise. Continuous vulnerability management in the cloud enables organizations to respond swiftly to emerging threats, reducing the time window for attackers to exploit vulnerabilities.

- Implement Network Segmentation and Access Controls
Network segmentation and robust access controls are fundamental to cloud security. By dividing the vulnerability management in the cloud environment into separate segments and implementing strict access controls, organizations can limit the lateral movement of attackers and contain the impact of potential breaches. Implementing firewalls, virtual private networks (VPNs), and role-based access controls (RBAC) helps ensure that only authorized personnel can access critical resources, reducing the attack surface and enhancing vulnerability management efforts.
- Foster a Culture of Security Awareness
In addition to technical measures, fostering a culture of security awareness is crucial for effective vulnerability management in the cloud. Educating employees about common security risks, best practices, and the importance of adhering to security policies helps create a vigilant workforce. Conducting regular security awareness training, phishing simulations, and encouraging reporting of suspicious activities can significantly enhance an organization’s ability to identify and address vulnerabilities in the cloud.
- Engage in Threat Intelligence Sharing
Staying informed about emerging threats and vulnerabilities is vital in today’s rapidly evolving threat landscape. Engaging in threat intelligence sharing initiatives, both within the organization and with external sources, can provide vulnerability management in the cloud insights into the latest attack techniques, vulnerabilities, and mitigation strategies. By leveraging threat intelligence feeds, organizations can proactively update their vulnerability management processes, ensuring they stay one step ahead of potential threats in the cloud.
- Continuously Assess and Improve Security Measures
Vulnerability management in the cloud is an ongoing process that requires continuous assessment and improvement. Regularly reassessing the effectiveness of security controls, vulnerability scanning tools, and incident response processes is crucial to adapt to evolving threats. Engaging in penetration testing, red teaming exercises, and security audits helps identify gaps and weaknesses that may have been overlooked. By embracing a continuous improvement mindset, organizations can enhance their vulnerability management practices in the cloud.
- Collaborate with Cloud Service Providers
Lastly, it is essential to foster a collaborative vulnerability management in the cloud with cloud service providers. CSPs have a vested interest in maintaining secure cloud environments and often provide additional security features and services that can complement an organization’s vulnerability management efforts. Engaging in regular communication with CSPs, leveraging their expertise, and understanding the security capabilities of their cloud offerings can significantlystrengthen an organization’s vulnerability management in the cloud.
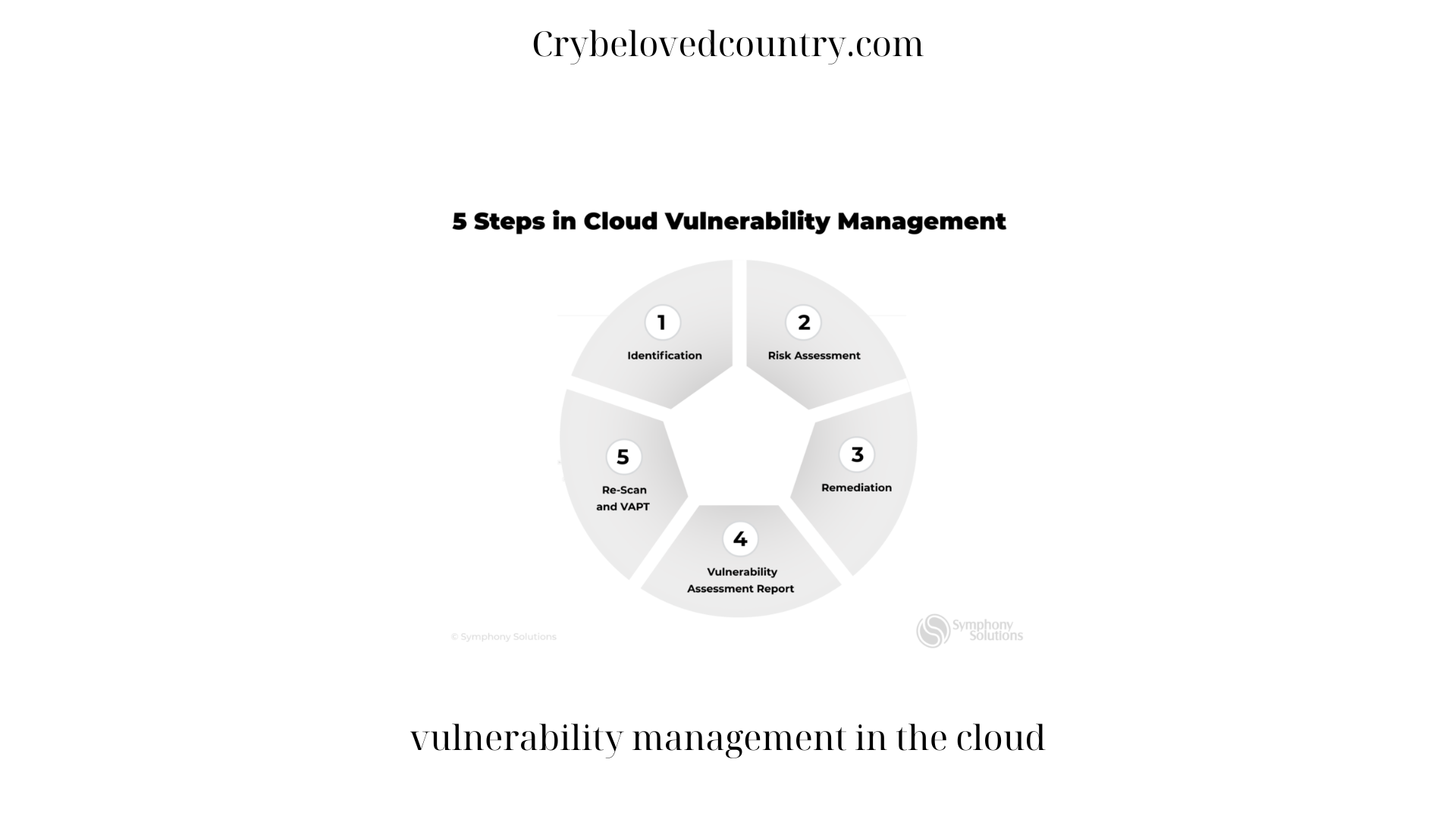
In conclusion, vulnerability management in the cloud is a critical aspect of ensuring the security and integrity of an organization’s data and applications. By understanding the shared responsibility model, conducting regular vulnerability assessments, implementing patch management processes, and employing secure configuration management, organizations can proactively identify and address vulnerabilities in their cloud environments.
Additionally, monitoring and analyzing cloud logs, implementing network segmentation and access controls, fostering a culture of security awareness, and engaging in threat intelligence sharing contribute to comprehensive vulnerability management. Continuously assessing and improving security measures, as well as collaborating with cloud service providers, further enhance an organization’s ability to secure their cloud environment effectively. By following these best practices, organizations can mitigate risks, minimize the potential for data breaches, and ensure a secure and resilient cloud infrastructure.